Mideye Shield
The authentication attack specialist
Block automated attacks before they reach your authentication system.
IP risk scoring that stops credential stuffing, password spray, and brute force attacks. Collaborative intelligence from every deployment.
Mideye Shield is a pre-authentication threat intelligence API — it scores IPs before they reach your authentication system, based on attack patterns observed across all participating customers. When one Shield customer is attacked, the collaborative network protects everyone else automatically.
What Challenge Does Shield Address?
Block lists go stale
Attackers rotate through IPs faster than any feed can update
Manual rules don't scale
Managing block lists and firewall rules manually takes time and leads to mistakes
Attack data stays local
What you learn from an attack doesn't help anyone else — and vice versa
How Does Shield Work?
Collaborative
Attack data from all Shield deployments feeds into a shared threat intelligence network. An IP flagged at one customer raises the score for everyone. Every authentication event — successful or failed — feeds back into the shared scoring model.
Adaptive
Scores decay over time. An IP that was malicious last week scores lower today if no new activity is observed. Real-time velocity scoring distinguishes bot patterns from legitimate users.
Curated
No block lists to maintain. No rules to configure. Shield returns a risk score (0-100) on every request. Your system decides what to do with it.
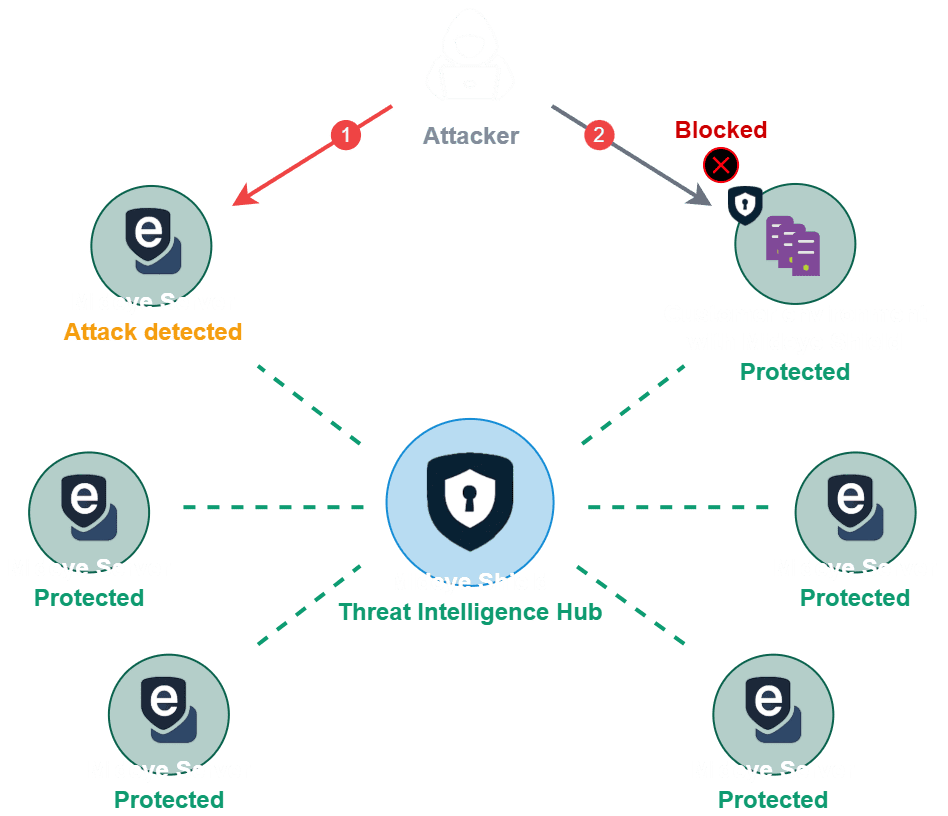
How Does the Network Effect Work?
When one customer is attacked, everyone learns. Instantly.
Day-one protection
Shield launches with a warm intelligence engine, drawing from aggregated, anonymized production data across multiple Nordic enterprises. No cold start. Production-proven detection from day one, based on attack patterns already observed across the network. Shield is included with Mideye Server 6.5.12 and later releases.
How Do You Integrate Shield?
REST API
Query the risk score for any IP with a simple HTTP call. Ingest authentication events to feed the network. Works with Python, Go, Java, Node.js, and any HTTP-capable stack.
RADIUS Backend
Integrates directly as a RADIUS backend module. No changes to existing authentication infrastructure. Inline protection for VPN, Wi-Fi, and network access.
RADIUS → Shield → Allow / Challenge / Block Why authentication-specific?
Shield focuses on authentication and access flows — credential stuffing, password spray, brute force. Different tools serve different purposes.
"I have a WAF"
WAFs protect web traffic. Shield protects authentication flows specifically, detecting patterns in login attempts that WAFs aren't designed to catch.
"I use IP reputation lists"
IP reputation flags known bad actors. Shield detects novel attacks and shares intelligence in real-time, including attacks from previously unknown IPs.
"I have MFA"
MFA prevents successful account takeover but doesn't stop credential stuffing attempts. Shield blocks the attempts before they reach your authentication system.
"We don't see many attacks"
You might not know. Most authentication attacks are silent. Shield gives visibility into what's actually hitting your login endpoints.
Collaborative. Adaptive. Curated.
Mideye Shield's shared threat intelligence and incident detection capabilities align with DORA Article 45 (threat intelligence sharing), NIS2 Article 21(2)(e) (incident detection), and operational security requirements for financial and critical infrastructure entities.
See our compliance hub for complete framework mappings.
Built by the team behind Mideye, protecting Nordic authentication infrastructure since 2005.
